
Flexible working hours and remote working provide numerous benefits to employers and employees. However, it also brings some cybersecurity challenges for both employers and employees. Almost 90% of IT experts consider remote workers are not secure. Around 70% of remote workers pose a bigger risk than onsite staff.
Whatever the security risks of remote working, you can put cybersecurity in place. Therefore, you must follow a few cybersecurity tips to stay protected whether you are an employer and employee:
› Use a Secure Internet Connection
Public networks and unsecured Wi-Fi are the major reasons for data breaching. In this situation, remote workers need to be told about how they can keep the company’s data safe. The simplest solution is to use a virtual private network (VPNs). In the VPN network, users can send and receive information safely, even over public networks. A VPN network allows remote users to access the corporate network while disguising the IP address and encrypting data traffic. Generally, the debate regarding the top VPN usually comes down to two; cyberghost vs nordvpn. However, every VPN is different and will meet different needs so it is always up to the user to decide which one to use.
› Manage Passwords
Passwords are as weakest as the remote employees in data security. Most employees are expected to handle their login details for different application accounts; here they leave a chance for data breaches. Password managers can mitigate this issue by supplying a safe way to IT departments. It helps to manage and store hundreds of passwords concurrently while making sure they are hard to crack into remote working areas.
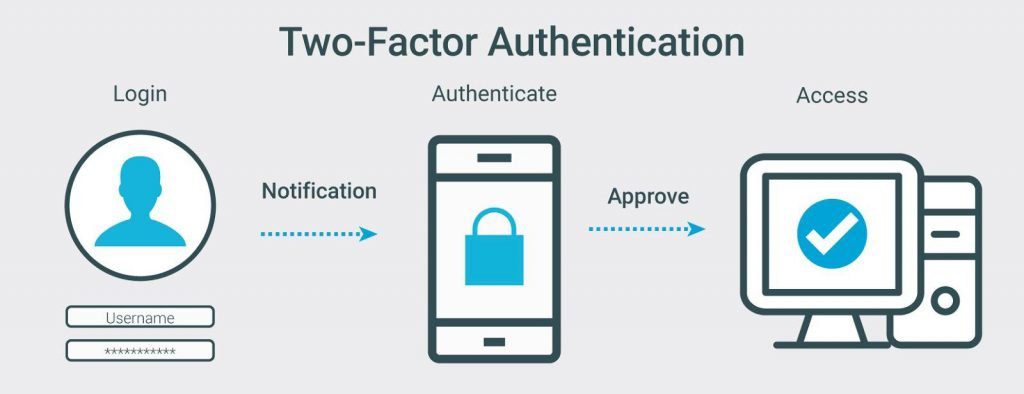
› Rely On Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA) includes an additional layer of security in account login. It confirms a user’s identity who is trying to access the system or account.
Once login information including username and password is entered, OTP (One Time Password) is sent on the user’s phone. This OTP changes every few seconds to stop third-party access whether it is done through email, text and so on. A user must enter the correct OTP to gain access. If you are going to go for this, you should make sure that the phone that will be used is as secure as it possibly can be to prevent this password falling into the wrong hands – you can click here to read about the security measures that you can encourage employees to take while they are working.
› Use Encryption Technology
Encryption is another way to secure organizations and their remote workers from data breaching.
Whether it is an application, software or a website, encryption technology can protect all of them. An organization can use different encryption software and program to secure their chatting or email communication. The most eminent programs are like Microsoft Office and Adobe Acrobat.
But for websites, you can install an SSL Certificate on website. It encrypts the sensitive data (Account login detail, Credit card information or Identification number) which is transmitted between users and a web server. For a multidomain website, you can also install a Multi domain SSL. Nowadays, SSL certificates are widely used for data security, they do not only protect sensitive information, but also boost sales, business credibility and conversion rate. Always work with SSL enabled websites.
It is also important to consider these measures when making important calls. That is why it may be a good idea to purchase a PGP phone (or a pgp telefoon kopen) when making such calls.
› Establish a Cybersecurity Policy
An organization must show their workers how important organizational data is. For showing this, they must make some data security policies and are strictly abided by the employees. Data security should always be an organizational priority.
You might be surprised by knowing that still numerous workers are unaware of the importance of data security both at the personal and professional levels. A data security policy should be signed while appointing any workers and it must have details of different security rules workers are expected to comply with.
› Update, Update And Update
It may seem unlikely but the IT department is always ready for cybersecurity, which may include software/hardware upgrades, user access improvements, and data recovery and data backups. Update the organization system’s software and applications are quite important as outdated software opens a window for cybercriminals. Other activities that are usually performed by IT professionals are network monitoring where they monitor infrastructure, workforce activities and take external audits to identify weaknesses of the network and reinforce defense action.
› Maintain Cyber Hygiene
Recent researches on IT show that around 60 % of IT experts consider security training to employees is the most effective way to stop security incidents. Security training works well for both in-house employees and remote employees. Each worker should know the dos & don’ts and when to avoid data sharing. For instance, if the cloud-based system is used in an organization, both the employer and their worker should know how to use it and how to keep the data safe and secure. Remote working policies or cybersecurity policies should not only be made, but understood, communicated, and practiced continually.
To Wrap Things Up
Implementing cyber securities is as important for your business as a promotion. Everything can go on stack including customer data, the company’s reputation and wealth if there is a little negligence in cybersecurity.
Employee’s education and training about cybersecurity is a must for every organization, as it is the first step toward your security plan and only well aware employees can abide by your security policies.
This is an article provided by our partners network. It does not reflect the views or opinions of our editorial team and management.
Contributed content
HedgeThink.com is the fund industry’s leading news, research and analysis source for individual and institutional accredited investors and professionals





































